BufferLab/AttackLab
Lab Assignment L3: The Attack Lab: Understanding Buffer Overflow Bugs (a.k.a. Buffer Lab)
Assigned: Oct. 23rd, Due: Friday, Nov. 7th. 11:59 PM
Download the Technical Manual here
Introduction:
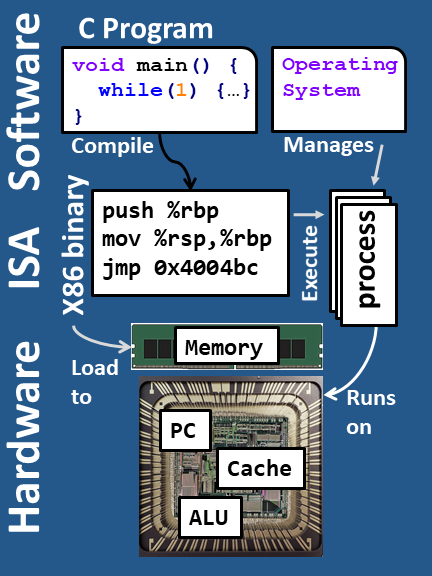
This assignment involves generating a total of five attacks on two programs having different security vulnerabilities. Outcomes you will gain from this lab include:
- You will learn different ways that attackers can exploit security vulnerabilities when programs do not safeguard themselves well enough against buffer overflows.
- Through this, you will get a better understanding of how to write programs that are more secure, as well as some of the features provided by compilers and operating systems to make programs less vulnerable.
- You will gain a deeper understanding of the stack and parameter-passing mechanisms of x86-64 machine code.
- You will gain a deeper understanding of how x86-64 instructions are encoded.
- You will gain more experience with debugging tools such as GDB and OBJDUMP. Note: In this lab, you will gain firsthand experience with methods used to exploit security weaknesses in operating systems and network servers. Our purpose is to help you learn about the runtime operation of programs and to understand the nature of these security weaknesses so that you can avoid them when you write system code. We do not condone the use of any other form of attack to gain unauthorized access to any system resources. You will want to study Sections 3.10.3 and 3.10.4 of the CS:APP3e book (Computer Systems: A Programmer’s Perspective) as reference material for this lab.
Get Your Files
You can obtain your files by pointing your Web browser at:
http://lnxsrv14.seas.ucla.edu:18213/
The server will build your files and return them to your browser in a tar file called targetk.tar, where k is the unique number of your target programs.
Note:
- It takes a few seconds to build and download your target, so please be patient.
Send the targetk.tar file to a (protected) Linux directory on the server in which you plan to do your work. Then give the command:
linux> tar -xvf targetk.tar.
This will extract a directory targetk containing the files described below. You should only download one set of files. If for some reason you download multiple targets, choose one target to work on and delete the rest. If your download fails constantly, we recommend trying the incognito browsing mode. YOu may have to click Keep in Google Chrome’s Downloads dropdown after pressing the submit button. If it still fails, you can reach out to benet@cs.ucla.edu.
If you see 0x0a (new line character) in the address of touch1, touch2, touch3 or at the top your stack, the target is faulty because the exploit string will be automatically truncated at that new line character. You can request for a new target from the website.
Warning:
If you expand your targetk.tar on a PC, by using a utility such as Winzip, or letting your browser do the extraction, you’ll risk resetting permission bits on the executable files.
The files in targetk include:
README.txt: A file describing the contents of the directoryctarget: An executable program vulnerable tocode-injectionattacksrtarget: An executable program vulnerable toreturn-oriented-programmingattackscookie.txt: An 8-digit hex code that you will use as a unique identifier in your attacks.farm.c: The source code of your target’s “gadget farm,” which you will use in generatingreturn-oriented programmingattacks.hex2raw: A utility to generate attack strings.
In the following instructions, we will assume that you have copied the files to a protected local directory, and that you are executing the programs in that local directory.
Getting Started
Once you have the lab files, you can begin to attack. To get started, download the pdf linked below. It is a technical manual which is a guide to to help complete each section of the lab.
Download the Technical Manual here
Logistics
- As usual, this is an individual project. You will generate attacks for target programs that are custom generated for you.
- We’ve made Phase 5 a bonus phase, so the total score for this lab is now 95 points instead of 100.
Handin
There is no explicit handin. The system will notify your instructor automatically about your progress as you work on it. You can keep track of how you are doing by looking at the class scoreboard at:
http://lnxsrv14.seas.ucla.edu:18213/scoreboard